We all love free public WiFi when we are travelling, ordering food in a restaurant, waiting for a job interview, doing internet banking, relaxing at a beach café or in a hotel lobby – it is so convenient! – but, so do criminals. It is o convenient that hackers have devised a number of ingenious attack techniques that take advantage of WiFi vulnerabilities (particularly ineffective security policies at public WiFi hotspots).
Wireless networks are generally more vulnerable to attack than wired networks. This is because data is transmitted using radio technology, which is difficult to contain over the air, instead of a dedicated cable, to which a thief needs physical access.
Much of the damage caused by WiFi attacks can be prevented by using digital security certificates. Indeed, WiFi attacks can be precluded by Extended Verification (EV) Secure Socket Layer (SSL) certification. In a nutshell, EV SSL protects users by encrypting their data and authenticating the parties in two-way communications over a network are who they say they are.
How secure is data transmitted over WiFi? And, what are the dangers when confidential information is stolen by attackers?
How vulnerable to cyber attack is WiFi?
According to Kaspersky Labs, one in four public WiFi hotspots globally are not secure, leaving users’ data open to easy interception by hackers. Kaspersky found that 25 percent of these networks did not utilize password protection or encrypt transmitted data.
On the home front, when people buy wireless devices, they often do not change default passwords or configure their devices securely. (You can use Shodan to see if your internet-connected device is publicly accessible.)
Worryingly, the tools attackers use to infiltrate public WiFi networks can be purchased cheaply at popular online eCommerce stores like Amazon or eBay, and there is plenty of open source software around that can be used to identify, and connect to, unsecure networks.
Why do you need wireless security?
General users and frequenters of public hotspots – Using SSL protects you and your family from identity theft and the loss of confidential data. Personal information fetches a high price on the digital black market. It can be used to scam you and people you know (e.g. by stealing your contacts list and harassing contacts); hijack your messaging apps; perform unauthorized financial transactions; steal data from your device and hold it to ransom; maliciously wipe your hard drives; and even embarrass you (by hacking and sharing your internet history, emails, or personal information).
After your identity is stolen, you may lose access to your accounts; be (temporarily) responsible for illegal actions performed in your name; face censure from friends, family, and colleagues; have to apply for new personal documentation; and face severe financial losses.
Business owners – When you can reassure your customers their data is secure and can demonstrate exactly how you are doing it, you build a more loyal customer base. When you secure network data, you save on the phenomenal potential cost of litigation when personal customer information is stolen. When you implement SSL, your Google rankings are improved and you are more likely to win new customers and reduce churn.
Using an SSL certificate cannot guarantee you won’t be attacked when using WiFi, but criminals won’t be able to do anything with the information they steal as it will be encrypted. There are other benefits –commercial and branding – particularly when you combine EV and SSL. We will cover these later.
SSL and EV certification acronyms and jargon
Digital certificates are signed and issued by a Certificate Authority (CA) – an entity that is allowed to verify ownership of the digital key shared by two parties in a transaction or communication – but not all certificates are equally effective. SSL and EV are two different types of security certificates, with the gold medal going to EV SSL certification.
SSL
SSL - and its successor Transport Layer Security (TLS) - is a cryptographic protocol that provides communications security over a computer network. It is used extensively in web, messaging, IoT, WiFi communication, Single Sign-On, Enterprise Mobility Management (EMM), and Voice over IP (VoIP) applications. (Incidentally, the differences between SSL and TLS are relatively minor and, for the purpose of this article, being completely transparent to the average user, irrelevant.) As the name denotes, SSL is the security layer between you and the client application, and is concerned with managing authentication (credential validation), data encryption, and data integrity. It is at the authentication level that SSL and EV differ.
SSL comes in two flavors: Domain Validation (DV) and Organization Validation (OV). DV – proven ownership of a domain – provides the least authentication. It is fine for your personal blog. If you are running a small website with minor data risks (e.g. customers don’t actually make purchases online), OV – where company registration has been verified by a CA – may be good enough for you.
EV
EV SSL certificates are like SSL certificates but running on digital rocket fuel. They differ at the level of authentication, not encryption. To be issued an EV certificate, a company must irrefutably prove its identity (physical address of the entity, business licensing information, proof of the right to use a particular domain name, etc.) to a trusted 3rd party. A browser scanning a certificate during a communication can tell what type of certificate it is and act accordingly.
EV SSL adds an extra layer of protection against phishing websites by showing the name under which a website is registered.
You can view details about a secure site by clicking on the padlock symbol in the address bar.
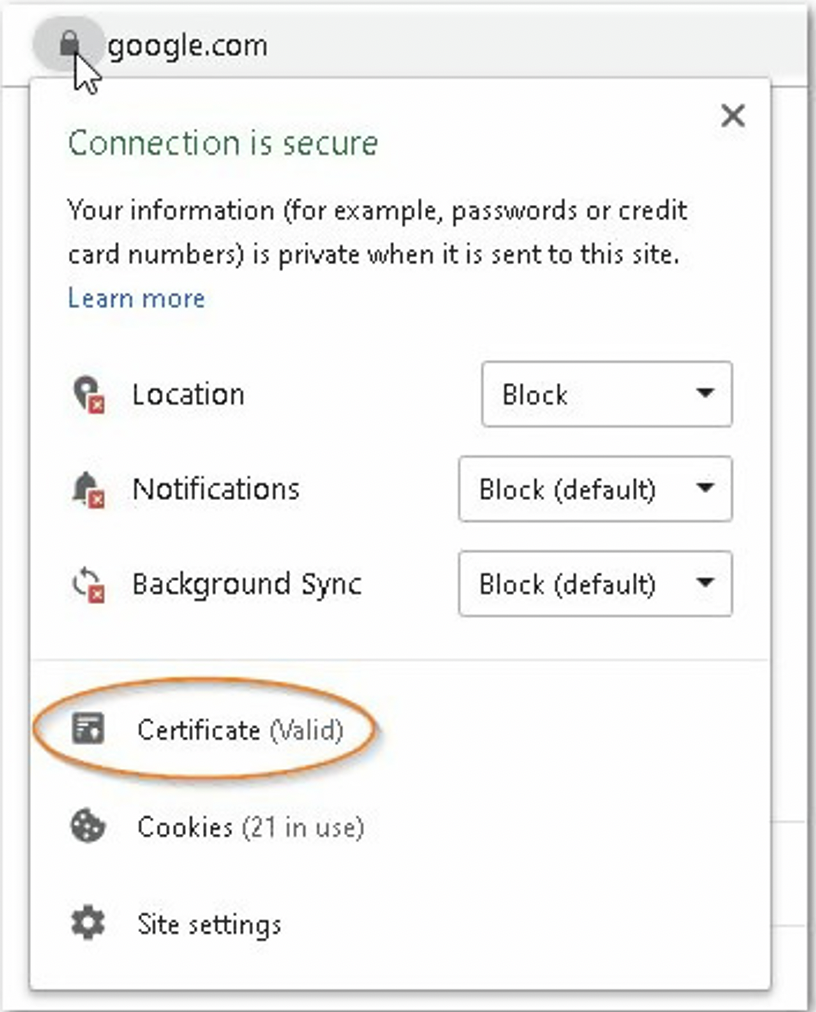
You can view details about an unsecure site by clicking on the information symbol in the address bar.
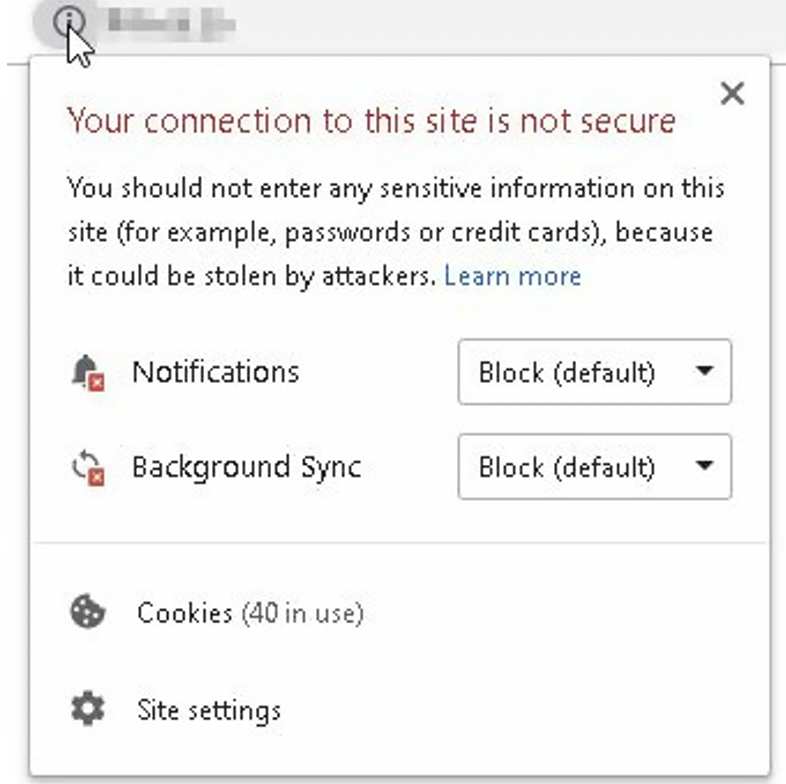
Protocols
A protocol is a standard that defines the rules which govern how endpoints in a network communicate and how information is transmitted. Endpoints include servers, individual devices, and applications.
Certificates
A digital security certificate is an electronic document comprising data files that associate a cryptographic key with an organization or application. What does this mean? It means that only the two parties in a transaction or communication who have the key (more about this later) can decrypt and view data being transmitted between them. For instance, when you log into your internet banking application, it is not just your password that keeps your account secure, it is the digital certificate that ensures your credentials are encrypted and inviolable.
Certificate authorities
The Certification Authority Browser Forum (CAB forum) outlines the requirements a legal entity (e.g. company, person, or website) must fulfill before being issued a certificate: Baseline Requirements for SSL certificates and Extended Validation Guidelines (EVG) for EV certificates.
Well known CAs include Comodo, Symantec, RapidSSL, GoDaddy, GlobalSign, and DigiCert.
Why do you need digital certification?
Its role is to keep your personal data safe from prying eyes and theft by eavesdroppers, hackers, and cyber criminals – whether opportunists, dedicated organized cyber criminals, or digital joy riders who hack for the so-called fun of it.
The acronym ACTED will help you remember the five-prong role of digital certificates:
· Authentication – Verifies a website belongs to whomever it says it does, e.g. it is not impersonating a branded website. A common trick by phishers is to create fake websites that mimic the real one, e.g. www.paypals.com versus www.paypal.com (the ‘s’ in the first URL is quite difficult to spot).
· Compliance – SSL certification is mandatory for compliance with numerous legal regulations, e.g. those for the Payment Card Industry (PCI).
· Trust – Provides reassurance for consumers, especially if they are making a purchase online or performing financial transactions. Trust is a necessary component to maintain brand loyalty and retain reputational integrity.
· Encryption – Encrypts data so that even if hackers do manage to intercept messages, they can’t read them.
· Device protection – The latest version of WiFi Protected Access (WPA) security protocol will soon be mandatory for all WiFi-enabled devices but is not a failsafe solution itself. CA provider Symantec’s Bruce McCorkindale suggests basic wireless security should include: SSL (or TSL) certification, the use of a VPN, and multifactor authentication.
Types of WiFi attacks
Interception attacks include Man-in-the-Middle (MITM), relay, and replay attacks, in all of which the criminal intercepts sent data before it can reach its intended endpoint. Impersonation attacks where criminals spoof genuine websites include Evil Twin and Rogue Access Point (RAP) attacks. Vulnerability scanning attacks are also tempting to cybercriminals precisely because people don’t always secure their devices and ensure their data is encrypted.
In all the below attack types, using SSL to encrypt data makes networks less vulnerable. Using EV ensures users only access genuine websites whose credentials have been independently (and rigorously) verified.
Dodgy links and redirects to fake websites
A hacker may design a website that looks very much like a genuine, popular website and lure a visitor into visiting by using phishing and social engineering techniques. For instance, you could get an email supposedly from your bank or a store with which you have an account, requesting you log in to the organization’s website to pay an outstanding balance, update your login details, confirm your identity, or even verify your debit orders are legitimate. Unless you are very alert, clicking on a fake link might direct you to a rogue website that looks very much like what you were expecting to see. Unfortunately, logging into this site will compromise your credentials (and the first thing the attackers will do is access your real account and change your login details. It may even be days before you revisit the site and discover the forgery.)
In the below example, the URL is not a genuine PayPal one.
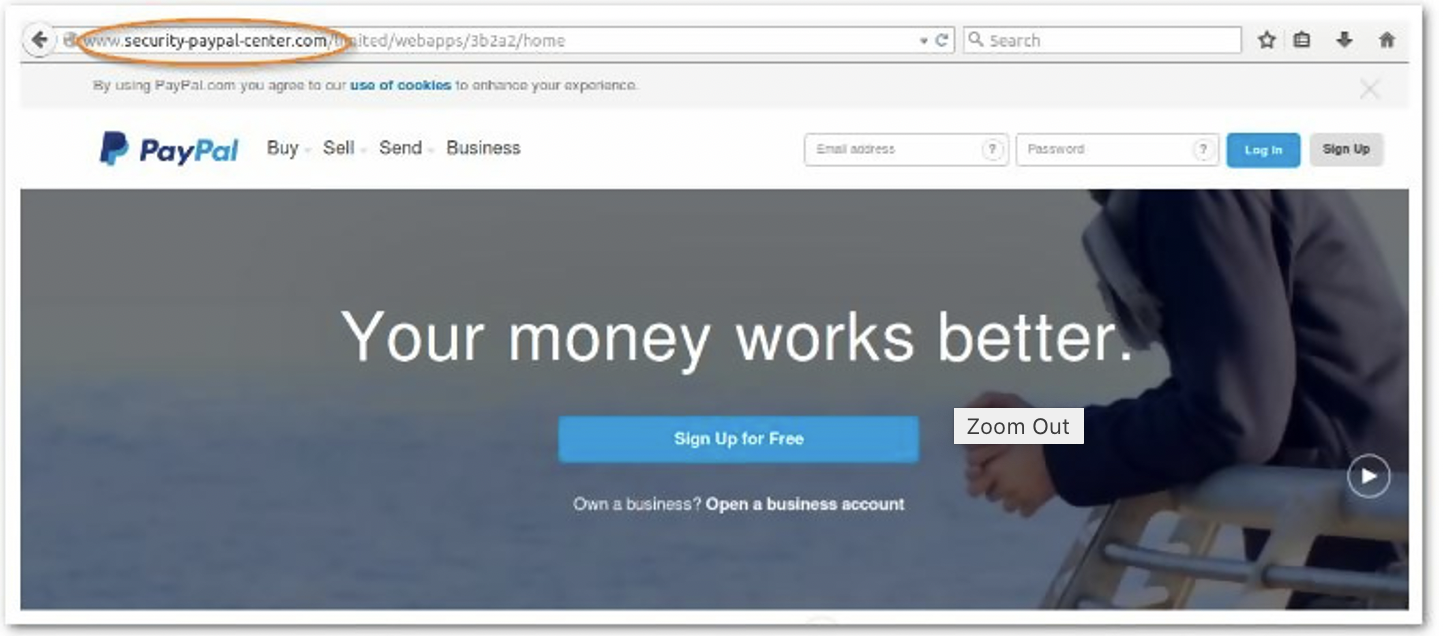
(Source: Cisco Umbrella)
War driving and vulnerability scanning
A study published by ResearchGate did a random scan of wireless networks in a sample of Dubai suburbs and found that 35 percent of networks did not employ security at all, and 26 percent used the outdated WEP protocol. These networks are targeted by opportunistic thieves (war drivers) who use scanning tools to identify vulnerable victims using WiFi devices. WiFi hacking tools can be purchased on eBay or Amazon very cheaply.
Eavesdropping
This odious and intrusive practice involves either scanning a network for vulnerable wireless access points (WLAN discovery), or listening in on a conversation between two parties. If data is not encrypted, it is easy for criminals to eavesdrop once they have a foot in the door. While the former practice is commonly employed legally by organizations to test the security of their systems, eavesdropping is illegal.
Evil twin attack aka Rogue Access Point (RAP)
This attack – and its partner-in-crime, the KARMA attack – involves an attacker setting up a rogue (fake) access point (AP) and luring visitors to use it. An example of this, reported by Bloomberg, was when a group of white hat hackers checked into a classy hotel and created their own hotspot, giving it the same name as the hotel. Within minutes, six guests had joined the spoofed (fake) hotel network, compromising their devices to the pretend hackers.
Fake APs are relatively easy for hackers to purchase and set up in free WiFi hotspots. Because public WiFi networks aren’t always well protected, attackers can use brute force (dictionary) attacks to compromise the public network and steal access credentials.
WiFi devices can’t distinguish between APs that use the same SSID, so criminals may disconnect a user’s device from the network, set up their own AP with the legitimate SSID and then start broadcasting with a high signal strength to tempt the disconnected device to re-connect to the fake AP.
In addition, in insecure wireless networks, AP credentials are often broadcast in plaintext across the network to subscriber nodes, making eavesdropping easy for attackers.
Physical tampering and built-in software flaws
An AP may be located at a public hotspot in a position where it can be physically tampered with by thieves, e.g. to reset the device to its original factory settings. A hacker can then Google the device’s default password in seconds.
In addition, vendor-specific software and hardware may have its own built-in vulnerabilities. There were, for instance, the reports of Orange LiveBox ADSL modems (over 19000 of them) leaking WiFi SSIDs and passwords in plaintext. It is not such a rare event. Recently, Linksys Smart WiFi routers (over 25000) were identified as leaking sensitive data, e.g. MAC addresses and configuration information, to remote hackers.
Packet analyzing and sniffing, and password theft
Often used innocuously by businesses to monitor their network traffic, attackers use these little programs to gather information about their potential victims on a network. The lowliest members of phishing gangs spend much of their time creating databases of information about their victims. Some of this information is used by criminal social engineers to engage with victims. Knowing about you enables them to personalize communications with you, thus engendering your trust.
When wireless traffic data is not encrypted, software tools like WireShark make it easy to capture and analyze high volumes of data packets. For instance, if a WiFi hotspot doesn’t use SSL and you log in to your accounts over a croissant and latte, criminals can intercept your credentials in plaintext.
Address Resolution Protocol (ARP) spoofing or poisoning
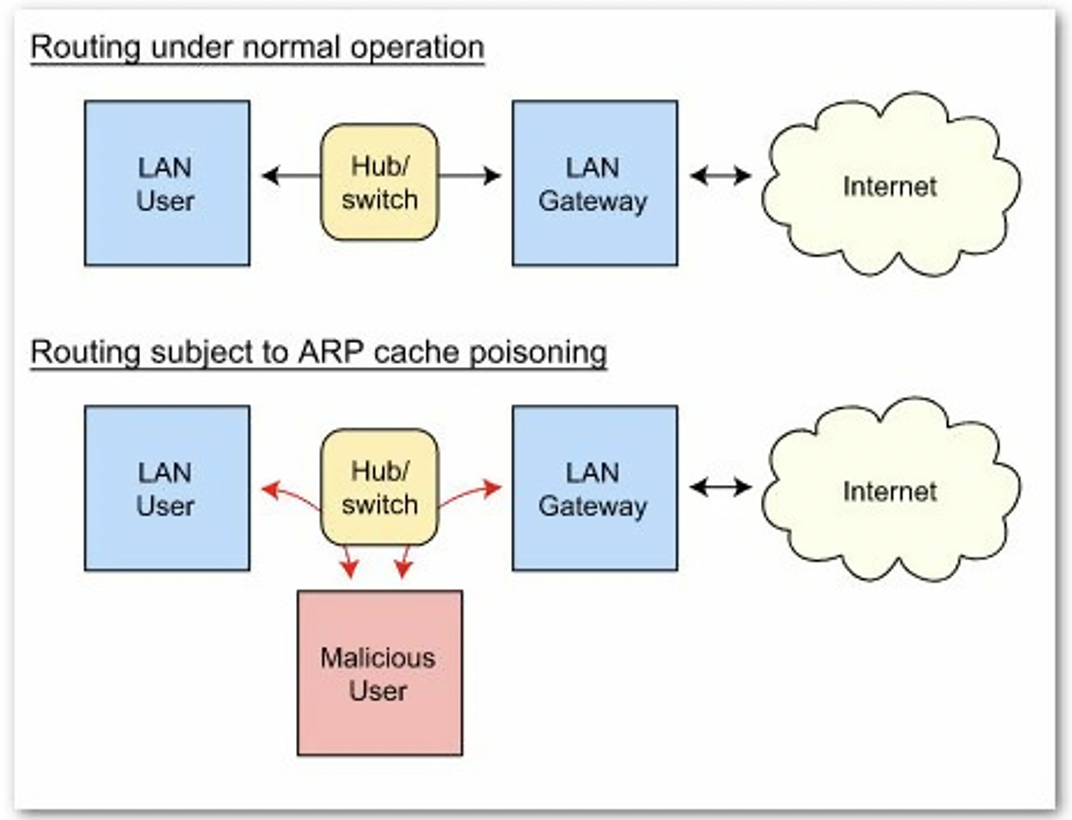
ARP spoofing (Source: Wikimedia Commons)
These types of attacks work with the criminal sending fake ARP communications to local area networks, and then modifying a device’s configuration and properties. Targeted particularly at WiFi communications, we can see just how easily an attacker is able to insert themselves between a genuine user and another endpoint. The ARP poisoning technique is used by attackers to substitute a device's Media Access Control (MAC) address with their own one. After a genuine user has sent a request over WiFi, the network computer, upon receiving it, unknowingly sends the reply to the hacker's computer (to the substituted MAC address.)
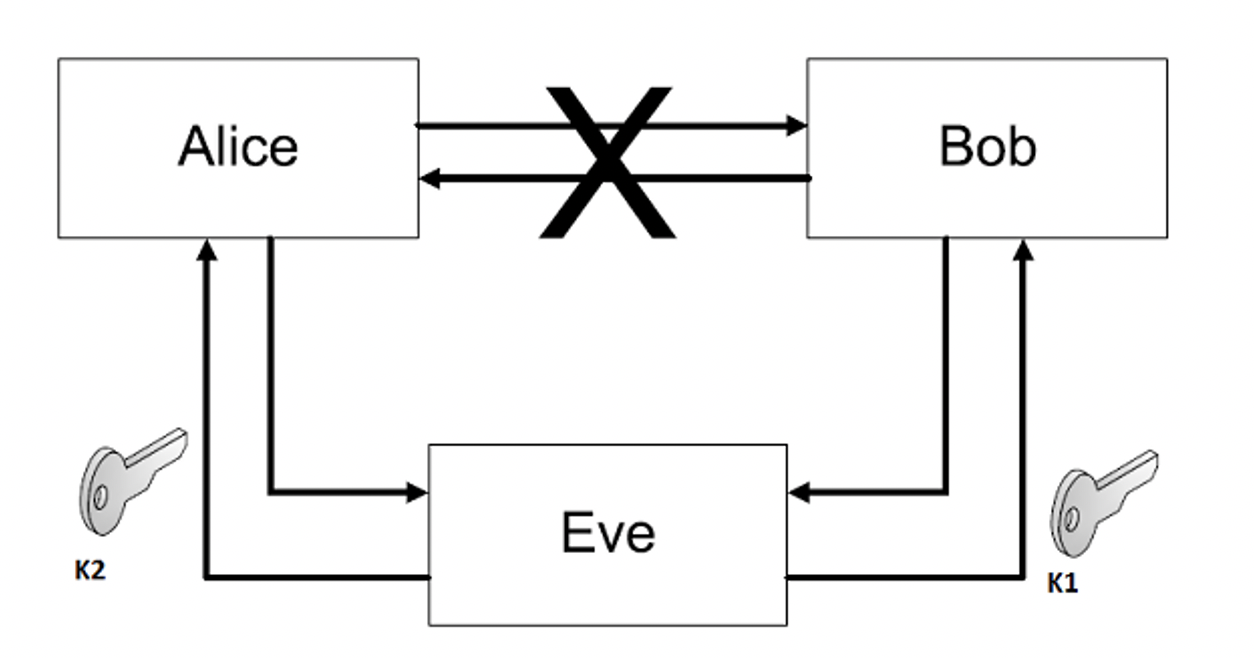
Man-in-the-Middle (MitM) attacks
Last but not least, MitM attacks are the bane of WiFi networks. A man-in-the-middle is an attacker who eavesdrops on communications between endpoints and can change the content of messages. For example, if in reception range of an unencrypted wireless device, a man-in-the-middle launches an interception attack by inserting themselves between an access point and user.
Man-in-the-Middle (Source: Wikimedia Commons)
The key to this strategy is impersonation. Both genuine parties in a communication are unaware they are not actually talking to each other but to the man-in-the-middle. A nice, real-world example was reported by CBC. Two men used this smoke-and-mirrors tactic to cheat on a medical school entrance exam: The first man, while taking his exam, used WiFi technology and a pinhole camera to transmit the test questions to his partner in crime who sourced expert answers to the questions and relayed them back to the first man. The experts in this case were three tutors who thought they were talking to a job interviewer: the second criminal and man-in-the-middle.
SSL in action – How does it work?
SSL uses Public Key Cryptography (PKC) to encrypt data between two endpoints (you and the website you are visiting) and ensure only the two of you can decrypt it. There are two types of PKC: asymmetric and symmetric. Symmetric encryption uses a single key, which needs to be shared between two parties before it can be used (for instance, you could email the key to them or give them a flash drive). Asymmetric encryption uses key pairs, a public and a private key. The public key is shared but the private one is not.
We’ll focus on paired PKC as it is more commonly used for website interactions.
On the internet, the complexities of cryptography are explained by Alice and Bob, two fictional characters who represent generic placeholders for IT entities, e.g. servers, networks, applications and devices. Below, Alice and Bob introduce asymmetric cryptography. You can also think of Alice and Bob as two entities: Alice is a WiFi device at a public hotspot wanting to log on to internet banking and Bob is the banking website.
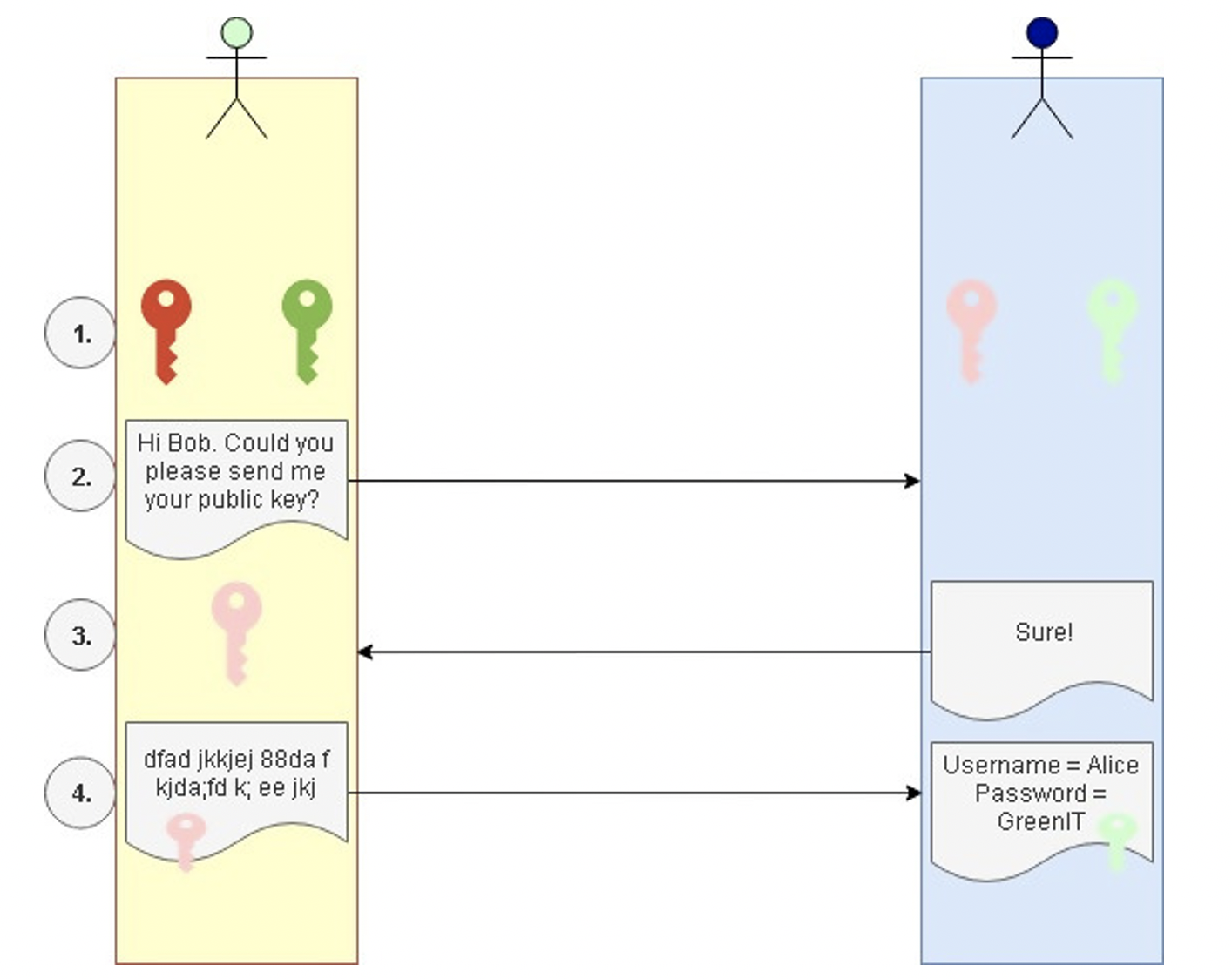
1. Bob and Alice, wise to the ways of cybersecurity, each create a public key (viewable by anyone) and a private key (known only to themselves and not to each other). These key pairs are matching: i.e. data encrypted with the public key of the sender can only be decrypted by the private key of the receiver.
2. Alice goes to Bob, her bank, and asks Bob for his public key. His public key is contained in the SSL certificate which Bob shares with Alice. (Note: An SSL certificate is sometimes referred to as a public key.)
3. Alice sends her login details to Bob, but first encrypts it with his public key.
4. Using his private key, which is matched to the public key he sent Alice in the SSL certificate, Bob decrypts Alice’s request.
Bob sends a virtual thumbs up to Alice and allows her to access his website.
Benefits of EV SSL
You would not drive a car without a seatbelt would you? With SSL, security is proactive – it mitigates the risks of a data breach.
Top ten benefits of EV SSL to mitigate WiFi threats
1. Establishes a secure HTTPs connection between two endpoints and maintains the integrity of data in transit.
2. Visibly reassures online shoppers their transactions and personal data are safe.
3. Mitigates the vulnerabilities associated with wireless device “backdoors”.
4. Encrypts data, including login credentials, when a user signs into and uses a confidential account, e.g. internet banking, and protects against opportunistic thieves at public WiFi hotspots.
5. Encouraged by search engines who give HTTPS websites higher SEO rankings, whether or not they are transmitting confidential information.
6. Verifies to engines like Google that a website is actively securing customer’s data.
7. Validates that a business entity’s registration details have been verified by a 3rd (trusted) party.
8. Can provide wildcard domain protection over an entire website and not just individual web pages.
9. Ensures a business website won’t be singled out with the latest version of Chrome by Google as “unsecure”.
10. Mitigates the threat of interception attacks like MitM.
Peace of mind
Peace of mind not only for a business, according to an Experien/Ponemon survey, 76 percent of respondents reported stress was the main factor affecting them after a data breach. Consumers tend to worry the most about having their password/PIN stolen and financial information, e.g. credit card details. Protecting this information is vital to any business storing consumers’ private data. With EV SSL, passwords, PINs, and other sensitive information is encrypted.
Non-compliance costs
According to CIO Dive, the cost of non-compliance with data regulations, including using SSL, is as much as $14.82-million compared to the actual cost of compliance, estimated at around $5.47-million.
Business share price
A study by Juniper Research found that cybercrime will hit businesses globally with a bill of over $2-trillion in 2019. The company estimates this is a four-fold increase from 2015. A Centrify/Ponemon study found that after a data breach was disclosed, the average share value index of a business’s stock dropped by, on average, five percent. Worse, the companies whose shares dropped the most found that after 120 days, shares prices still had not fully recovered. EV SSL certification reassures users to your website, your business has been authenticated and their personal information is encrypted while they do business with you.
Deters criminals from selecting you as their next victim
If your website is protected by SSL, cybercriminals will be less inclined to attack or spoof it and, like potential real-life burglars, will likely move on to a more vulnerable and easier target.
Mitigates reputational damage and bad publicity
The Centrify/Ponemon study mentioned above found that data breaches had a measurable impact on a company’s reputation. Of 113 organizations that experienced a breach, ones with a “weak security posture” noticed a seven percent increase in customer churn. It gets worse. 31 percent of customers actually walked away from doing business with the company and 65 percent said they had lost trust in the organization.
Protects sensitive data and lessens breach costs
Reported by Fox Business, Equifax will pay up to $425-million to customers affected by its 2017 data breach. That includes a payout of $25 an hour for the time consumers spent addressing the financial fallout.
Overall, the average cost of a data breach is estimated at $3.92-million. But, it is not only large corporations that are affected by cyber attacks. For small businesses, says IBM, even the smaller costs – on average $2.5-million for businesses with fewer than 500 employees – may have a bigger impact, often putting them out of business altogether. The IBM study found that the “extensive use of encryption” was a top cost-saver, reducing breach costs by as much as $360,000.
Builds customer trust and improves Google rankings
Google has already implemented a measure to identify websites that don’t have digital certification as “not secure”. Since July 2018, insecure sites are being flagged as such in Chrome’s address bar to make users aware that HTTP sites are not secure.
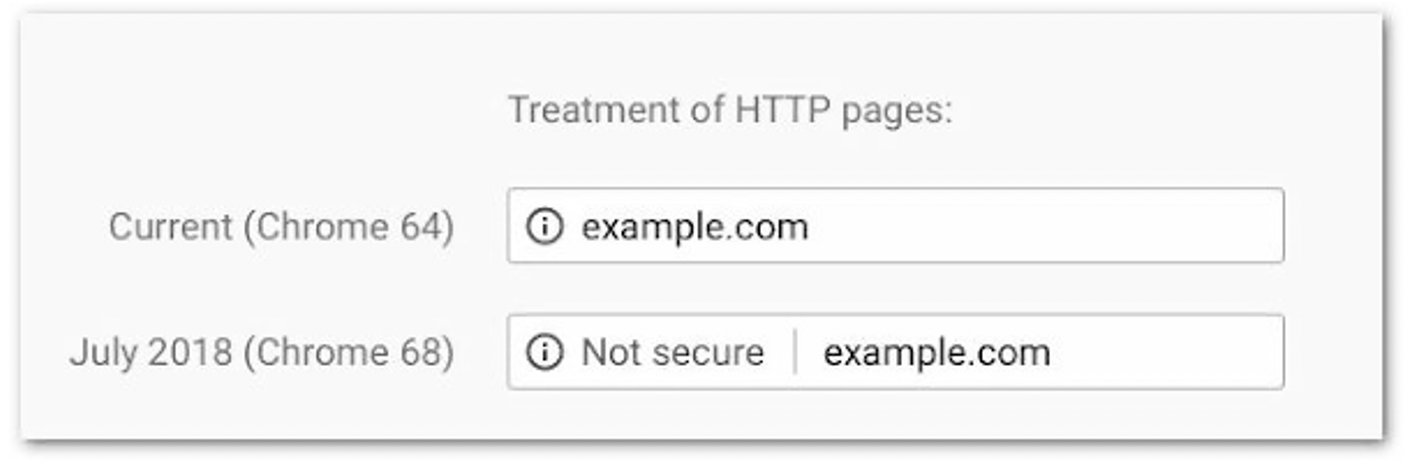
Search ranking and security (Source: Google Security Blog)
According to Google, HTTPS is cheap and easy to implement, and there is really no reason not to use it.
This move will have a major impact on businesses that don’t use SSL: a potential loss of customers and revenue, as well as reputational damage to an organization’s brand.
How EV SSL certificates protect you on WIFI
In conclusion, cybersecurity necessitates an holistic approach – e.g. using a reliable VPN, employing security professionals to secure your system, keeping software updated, etc. One of the methods to enhance security is using EV SSL certificates.
Alone, SSL is good, but EV SSL is better and is recommended, because it confirms the identity of whom you are communicating with, mitigating impersonation and interception issues, the prime attack threats to WiFi users.
In addition, EV SSL suppliers may provide insurance against losses in the event of a data breach.
In conclusion, cybersecurity necessitates a holistic approach – e.g. using a top VPN for Mac. or any other device, employing security professionals to secure your system, keeping software updated, etc. One of the methods to enhance security is using EV SSL certificates.



