In the realm of cybersecurity, OpenSSH stands as a titan, providing the foundation for secure communications across insecure networks. It's not merely a protocol; it's a comprehensive solution ensuring data encryption, connection integrity, and operational continuity. From managing remote servers to facilitating secure file transfers, OpenSSH is an indispensable tool in any cybersecurity professional's toolkit.
This vulnerability is a hacker’s dream. If exploited, it allows for full system compromise, enabling attackers to install malware, manipulate data, and create persistent backdoors. It can facilitate lateral movement within a network, allowing attackers to infiltrate other systems seamlessly.
Unveiling regreSSHion: A Dangerous Vulnerability Resurfaces
A critical Remote Code Execution (RCE) vulnerability has been uncovered within the OpenSSH server (sshd) on Linux systems utilizing glibc. This flaw, now identified as CVE-2024-6387, stems from a race condition in signal handling that can be exploited to execute arbitrary code with root privileges. In essence, this vulnerability provides attackers with a backdoor to systems, bypassing normal authentication procedures.
Global scans reveal a staggering 15 million potentially vulnerable OpenSSH instances, with approximately 750,000 directly exposed to the internet. This vulnerability is particularly concerning as it represents a resurgence of the previously addressed CVE-2006-5051, which has inadvertently been reintroduced in OpenSSH 8.5p1 (released in October 2020). This regression underscores the crucial importance of comprehensive regression testing in preventing the reemergence of resolved security issues.
The Fallout: A Cybercriminal's Arsenal Expanded
The implications of this vulnerability are far-reaching and severe. If successfully exploited, it grants attackers unfettered access to compromised systems, enabling them to deploy malware, alter critical data, and establish persistent access points. Moreover, it can serve as a springboard for lateral movement within networks, allowing malicious actors to infiltrate connected systems with ease.
With root-level access, attackers can circumvent traditional security measures such as firewalls and intrusion detection systems, rendering their activities nearly undetectable. The potential for massive data breaches and exposure of sensitive information to unauthorized parties is alarmingly high.
Mitigating the Threat: Urgent Actions Required
- Immediate Patching: Apply the latest OpenSSH security updates without delay.
- Access Restrictions: Limit SSH access to trusted networks and implement strong authentication methods.
- Network Isolation: Employ robust network segmentation to contain potential breaches.
- Enhanced Monitoring: Deploy advanced intrusion detection and prevention systems to identify and block suspicious activities.
Vulnerability Detection Across Platforms
Various security vendors have released detection rules for this vulnerability across different operating systems. Here's a brief overview of typical detection capabilities:
- Alpine Linux
- Fedora
- SUSE Enterprise
- Amazon Linux
- Gentoo Linux
- VMware Photon OS
- Google Container OS
- Oracle Enterprise Linux
- FreeBSD
- Debian/Ubuntu
- OS Agnostic
Many vendors are working on updates to include detection capabilities for Red Hat systems.
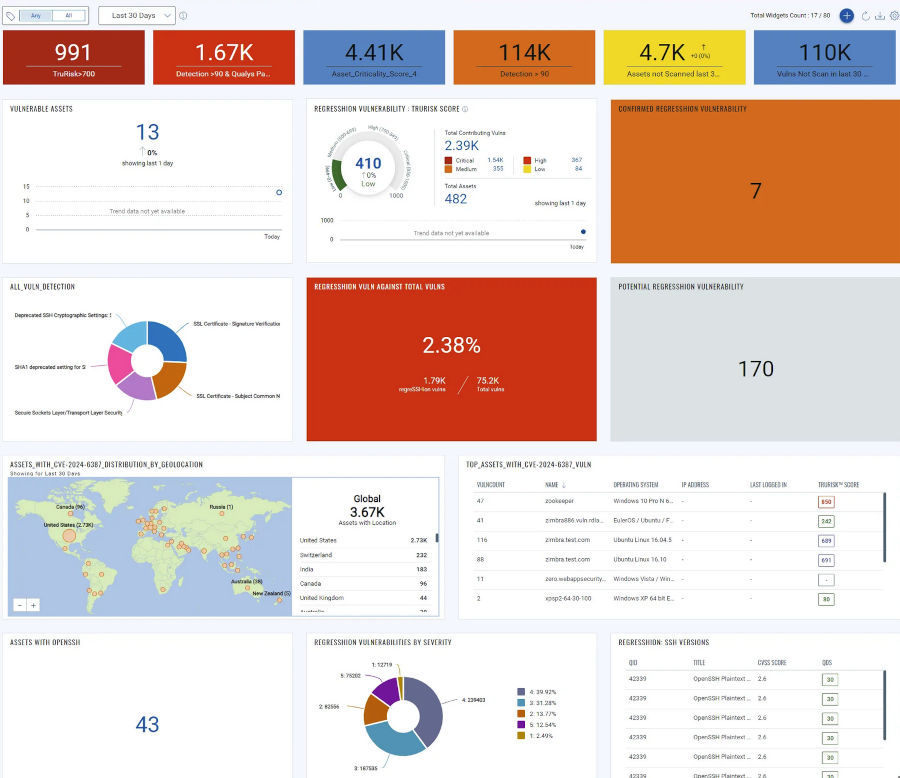
Identifying and Protecting Vulnerable Assets
Locating vulnerable assets is crucial in addressing this security issue. Modern asset intelligence platforms offer powerful capabilities to identify all internet-facing systems running vulnerable OpenSSH versions.
For comprehensive protection, unified security platforms provide end-to-end visibility and protection against vulnerabilities like regreSSHion. Security teams can utilize queries similar to the following to pinpoint affected assets:
vulnerabilities.cve_id:CVE-2024-6387
Centralized vulnerability management dashboards allow security professionals to monitor vulnerability exposure and orchestrate remediation efforts in real-time, offering clear visualization of impacted systems, their current status, and overall progress in risk mitigation.
Automated Remediation
Advanced patch management solutions can automatically deploy security patches for this vulnerability as soon as they become available, ensuring systems are protected without manual intervention.
Container Security
For organizations using containerized environments, it's crucial to detect and remediate CVE-2024-6387 across container deployments. Security teams should implement container-specific security measures and use appropriate queries to identify vulnerable containers.
Frequently Asked Questions (FAQs)
Is the regreSSHion vulnerability remotely exploitable?
Yes, it allows for unauthenticated remote code execution as root.
Why is it called "regreSSHion"?
It's a play on the term regression, highlighting that this bug is a reappearance of a previously fixed issue in OpenSSH.
Should organizations patch this urgently?
Absolutely. Patch all internet-facing assets immediately.
Does this affect macOS or Windows?
Windows is not affected. macOS may be vulnerable, but further analysis is needed to confirm exploitability.
How can users identify exploitation attempts?
Look for numerous "Timeout before authentication" entries in your logs.
Stay secure and vigilant. For more information and updates, visit cyberssl.com.



