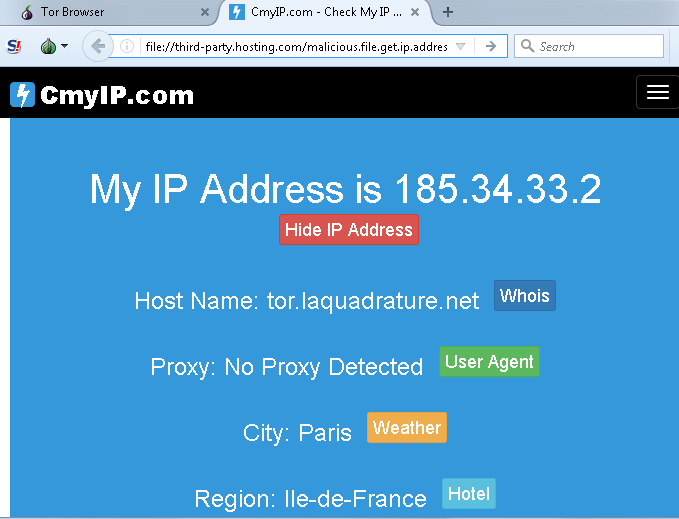
The Tor browser unmasks the user's IP address under certain circumstances - so surfing anonymously is out of the question.
With the Tor Browser Bundle, the Tor project offers a complete package for anonymous surfing, whereby users can do without a complicated configuration of their own browser or the Tor client.
Now it became known: The Mac and Linux versions of the Tor browser give the IP address of the user in certain circumstances, but the Windows and the alpha version of the Tor browser are not affected. At least the Windows version doesn't have a known vulnerability of exposing the IP address while surfing.
In order to lose the anonymization, a user only has to click on a link beginning with file: // (instead of about https: //). To put it simply, the operating system obviously tries to open this link on the Tor browser; however, the web server then communicates directly with the computer and not indirectly via the Tor network - and thus learns the IP address.
The vulnerability was originally discovered by Italian researcher Filippo Cavallarin, which also affects the Firefox Browser.
Even if the situation with the browser should occur infrequently, this vulnerability can be used simply for deanonymizing of users. The bug has already been fixed as part of an update.



